OPENSSL
Intro(OPENSSL) #
证书类型 #
暂时记录一个 x509 ( rfc, wiki)。这种格式一般广泛应用于Web浏览器和服务器之间的SSL/TLS加密通信。
对于这种证书的编码格式有 der, pem(privvaccy-enhanced mail) 等。且可以认为 pem 是 der 二进制的一种 base64编码。可以如下验证:1.下载网站证书并写入到文件:(不是直接下载,而是在 https 握手过程中会携带 证书数据,openssl 会在这个过程中打印出来,然后我们用工具提取即可)1.1.openssl s_client -connect wtfu.site:443 > pubkey.pem(运行可能会卡住,CTRL+c 终止就行)
查看 pubkey.pem 内容:删除-----BEGIN CERTIFICATE-----和-----END CERTIFICATE-----之外多余的内容。1.2.或者一步到位:openssl s_client -connect wtfu.site:443 </dev/null 2>/dev/null | sed -n '/BEGIN CERTIFICATE/,/END CERTIFICATE/p' > pubkey.pem2.转换:pem -> der,将除了第一行和最后一行的内容进行 base64 解码,然后写入文件sed '1d;$d' pubkey.pem | base64 -d > pubkey.der3.提取 pem 证书中的公匙并显示相关信息:openssl x509 -in pubkey.pem -pubkey -noout | openssl ec -pubin -text -noout4.提取 der 证书中的公匙并显示相关信息:openssl x509 -in pubkey.der -pubkey -noout | openssl ec -pubin -text -noout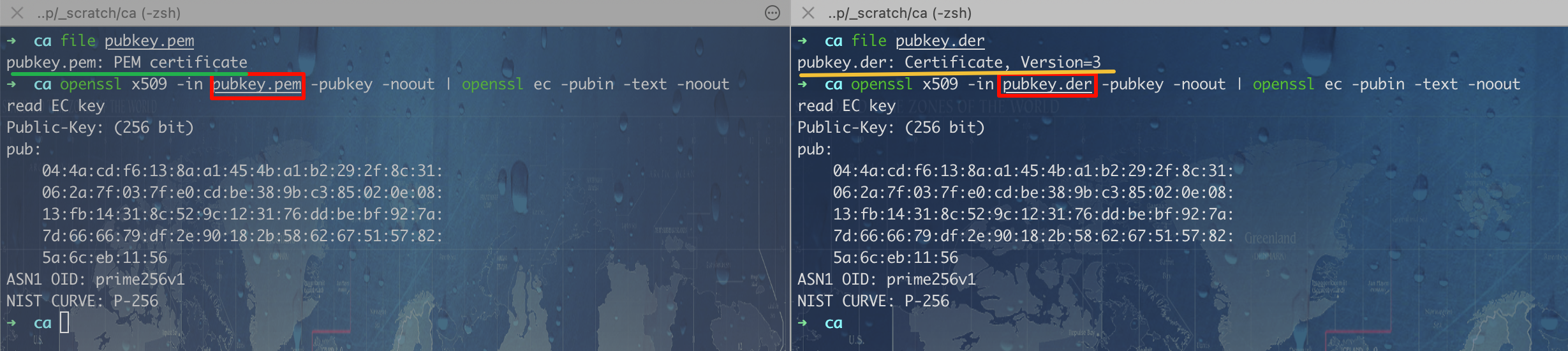
或者也可以通过 asn1在线解析 查看 pubkey.der 文件是否正确(DER 本质上是 ASN.1 结构类型的)。
另外可以计算 sha-256 指纹(对应 chrome 浏览器证书基本信息中的值),包括 证书和公匙
证书:cat pubkey.der | shasum -a 256,或者grep -v ^- pubkey.pem | base64 -d | shasum -a 256。
公匙:openssl x509 -in <pubkey.der | pubkey.pem> -pubkey -noout | grep -v ^- | base64 -d | shasum -a 256。Caution
上述服务器
wtfu.site当前密匙交换算法采用的是ECDHE,而不是 RSA,读取的时候需要按照ECDHE的方式解析,所以后面使用了ec。Referene #
证书指纹 #
Tip
chrome 浏览器查看的指纹是 sha256 算法的,腾讯云证书控制台详情显示的是 sha1 的。
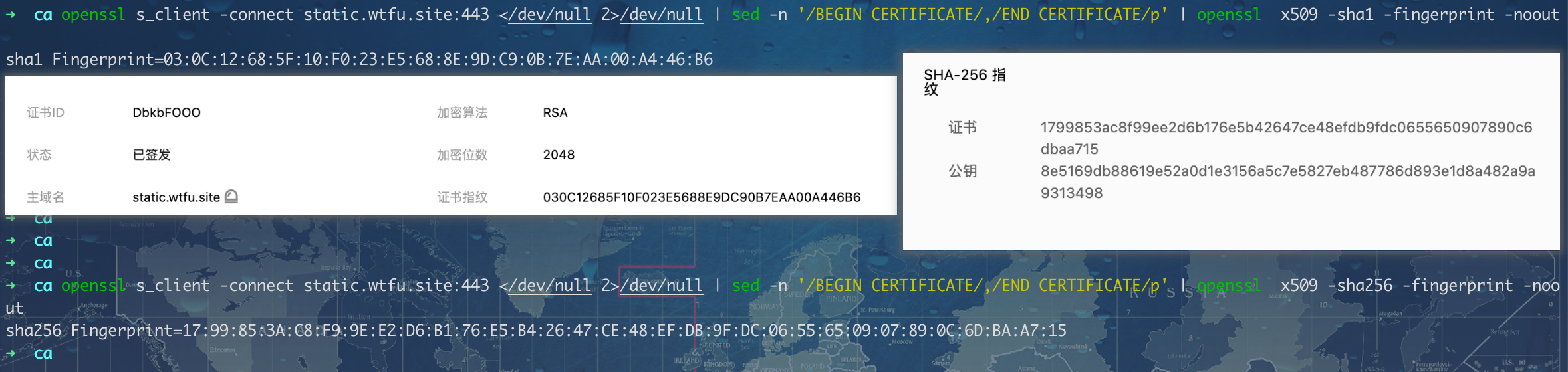
由上面信息也可以猜测到:证书的指纹 是指对当前证书所有二进制内容的算出的信息摘要。一般有 sha1,sha256 等。验证如下:获取到证书的二进制内容,然后进行哈希算出摘要。openssl s_client -connect static.wtfu.site:443 </dev/null 2>/dev/null | sed -n '/BEGIN CERTIFICATE/,/END CERTIFICATE/p' | grep -v ^- | base64 -d | sha1OPENSSL读取ssh-keygen生成公匙信息 #
简单记录一下使用 openssl 读取由 ssh-keygen 生成 RSA 类型的公匙信息,当然私匙也是可以的。
准备公私匙数据:ssh-keygen -t rsa -b 1024 -C 12302@wtfu.site,填写生成文件路径 /path/to/ca/ssh,就不加密码段(passphrase)了。
比如生成的公匙叫ssh.pub,私匙叫ssh。解析 RSA 公匙信息
1.直接使用 -e 选项导出 PEM 格式的公匙,然后去除第一,最后一行,转码后交给 openssl rsa 解析就行:ssh-keygen -f ssh.pub -e -m PEM | sed '1d;$d' | base64 -d | openssl rsa -pubin -modulus -text --noout。
且此处的公匙文件可以用私匙文件代替,因为当前生成的私匙里包括生成公匙需要的信息。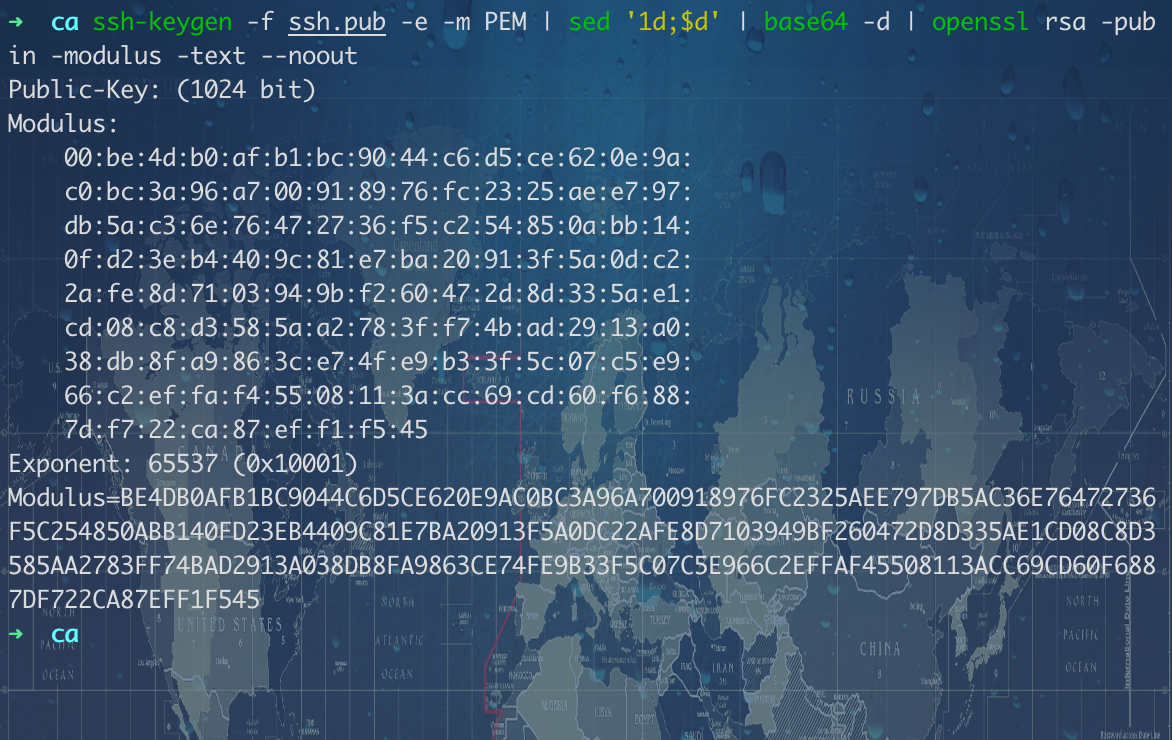
解析 RSA 私匙信息
1.记得备份原来的私匙文件:cp ssh ssh_bak,因为后续操作会将转换后内容的对私匙进行覆写,暂时没有找到其他好办法。2.判断起始和结束标记,是否是RSA类型的,是的进行下一步,如果是OPENSSH则进行 openssh 转换,如果是其他的,我也不知道了。
openssh 转 rsa:ssh-keygen -f ssh -m PEM -p,一路回车,查看 ssh 文件开始结束标记已经变成 RSA 了。3.查看私匙信息:openssl rsa -in ssh -text -noout | head -n 15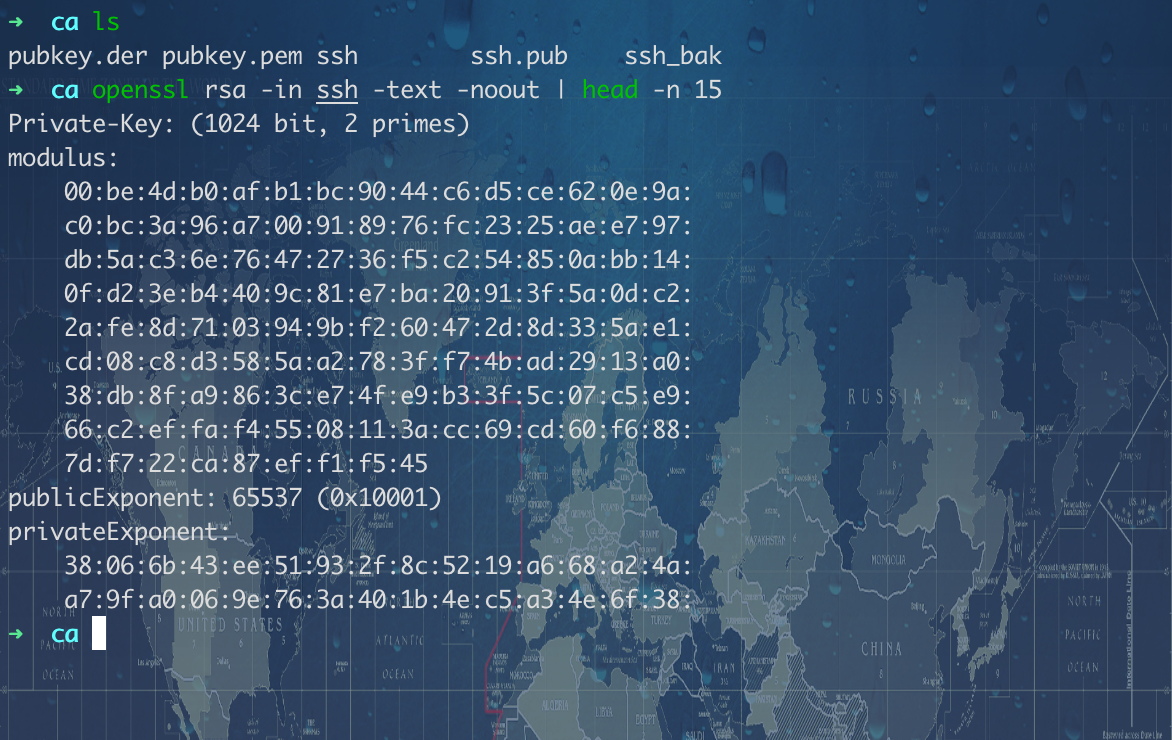
OPENSSL提取公私匙信息 #
OPENSSL操作示例 #
ADB 添加系统证书方法 #
一,cer格式证书文件计算步骤 #
二, pem格式证书计算步骤 #
三,der格式证书 #
四,上传至手机/system分区 #
自签证书 #
使用 openssl 自签证书给 burpsuite 代理使用,并且制作 android10 系统证书,捕获手机流量(手机抓包)。
解决 burpsuite–> android (NET::ERR_CERT_VALIDITY_TOO_LONG)
证书摘要: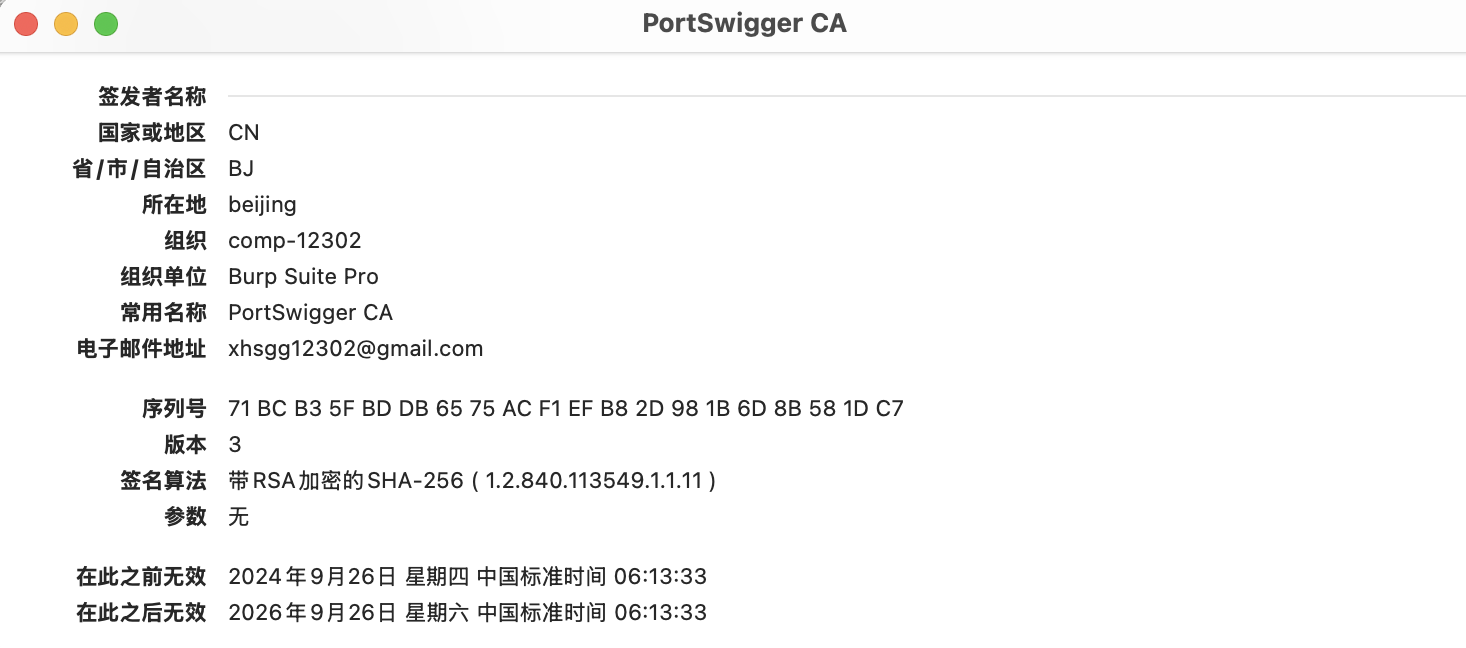
Caution
需要注意使用的
openssl.cnf配置文件,最终使用了/usr/local/etc/openssl@3/openssl.cnf。不知道是版本不对,还是修改过里面的东西,导致出现如下问题:
burpsuite 端 : Received fatal alert: decrypt_error
curl 端 :SSL routines:CRYPTO_internal:block type is not 01、SSL routines:CONNECT_CR_KEY_EXCH:bad signature
伪随机字节 #
openssl-rand: openssl 库可以生成位随机字节,并通过 base64 编码或这 hex 十六进制的形式打印输出,而且长度可控。基本使用如下:
openssl rand -hex 32openssl rand -base64 16记录 #
Reference #